Check Point Research (CPR), the Threat Intelligence arm of Check Point® Software Technologies Ltd. (NASDAQ: CHKP), a leading provider of cybersecurity solutions globally, has published its Brand Phishing Report for Q4 2022. The report highlights the brands that were most frequently imitated by cybercriminals in their attempts to steal individuals’ personal information or payment credentials during October, November and December of last year.
Yahoo was the most impersonated brand for phishing attacks during Q4 2022, climbing 23 places and accounting for 20% of all attempts. Check Point Research found cybercriminals distributing emails with subject lines that suggested a recipient had won awards or prize money from senders such as ‘Awards Promotion’ or ‘Award Center’. The content of the email informed the target that they had won prize money organized by Yahoo, worth hundreds of thousands of dollars. It asked the recipient to send their personal information and bank details, claiming to transfer the winning prize money to the account. The email also contained a warning that the target must not tell people about winning the prize because of legal issues.

Subscribe to our Telegram channel to get a daily dose of business and lifestyle news from NHA – News Hub Asia!
In general, the technology sector was the industry most likely to be imitated by brand phishing in the last quarter of 2022, followed by shipping and social networks. DHL came in second place with 16 per cent of all brand phishing attempts, ahead of Microsoft in the third spot with 11 per cent. LinkedIn also returned to the list this quarter, reaching fifth place with 5.7 per cent. DHL’s popularity could be due to the busy online shopping season surrounding Black Friday and Cyber Monday, with hackers using the brand to generate ‘fake’ deliveries notifications.
Omer Dembinsky, Data Group Manager at Check Point Software said: “We are seeing hackers trying to bait their targets by offering awards and significant amounts of money. Remember, if it looks too good to be true, it almost always is. You can protect yourself from a brand phishing attack by not clicking on suspicious links or attachments and by always checking the URL of the page you are directed to. Look for misspellings and do not volunteer unnecessary information.”
Top 10 Most Imitated Brands
Below are the top brands ranked by their overall appearance in brand phishing attempts:
- Yahoo (20%)
- DHL (16%)
- Microsoft (11%)
- Google (5.8%)
- LinkedIn (5.7%)
- WeTransfer (5.3%)
- Netflix (4.4%)
- FedEx (2.5%)
- HSBC (2.3%)
- WhatsApp (2.2%)
Instagram Phishing Email – Account Theft Example
CPR observed a malicious phishing email campaign that was sent from “badge@mail-ig[.]com”. The email was sent with the subject “blue badge form”, and the content tried to persuade the victim to click on a malicious link claiming that the victim’s Instagram account had been reviewed by the Facebook team (the owner of the Instagram brand) and deemed eligible for the Blue Badge.
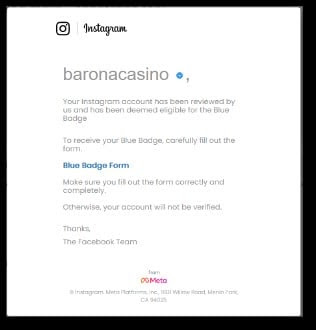
![Figure 2: Fraudulent login page https://www[.]verifiedbadgecenters[.]xyz/contact/ | Photo by Check Point Research](https://www.newshubasia.com/wp-content/uploads/2023/02/BlueBadges-phishing-email-2_CheckPoint.jpg)
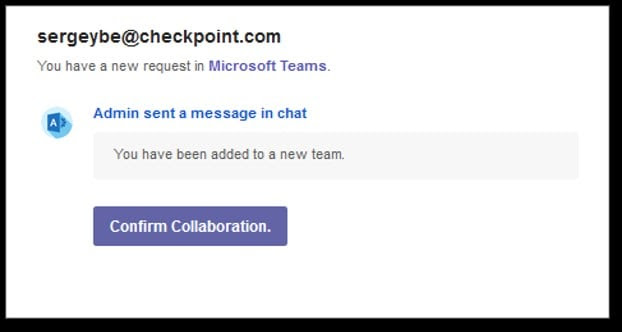
Microsoft Teams Phishing Email – Account Theft Example
In this Phishing email, Check Point Research found an attempt to steal a user’s Microsoft account information. The email was sent under a fake sender’s name – “Teams” with the subject “you have been added to a new team”.
The attacker tries to lure the victim to click on the malicious link claiming that they have been added to a new team in the app. Choosing to confirm the collaboration leads to a malicious website, which is no longer active.
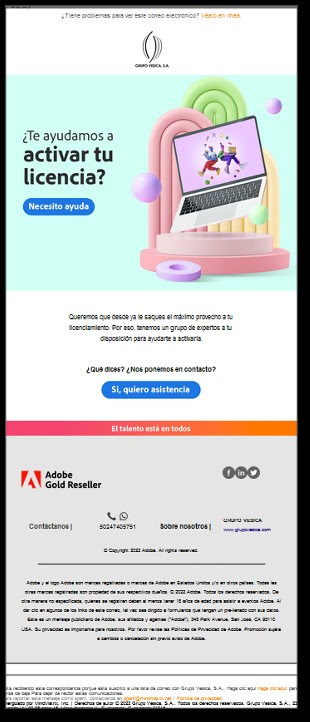
Adobe Phishing Email – Account Theft Example
This phishing email, which uses Abode’s branding, sent an email with its subject, originally in Spanish, reading – “Activate your license! Take advantage of its benefits” (originally: “¡Activa tu licencia! Aprovecha sus beneficios”). In the email the victim is encouraged to contact experts to help utilise the application license.
Clicking the link in the email opens a new draft message in Outlook addressed to a foreign email (not associated with Adobe), in which the user is asked to insert credit details and information for the “activation” of the license.
Source: Check Point Research




