While the disruptive impact of the Russo-Ukrainian conflict on the cyber landscape has relatively reduced in recent months, the threat landscape has returned to a state of “normality.” This new normal is characterised by an increase in cyberattacks, as this report unravels the use of new evasive tactics, frequent hacktivism-based attacks, and a daily barrage of ransomware targeting numerous organisations. Despite the waning effect of the conflict on the cyber threat landscape, the persistence of these threats highlights the ongoing need for heightened vigilance and robust cybersecurity measures to counteract the relentless and evolving nature of cyberattacks.

In recent months, we have reported the unravelling of a Chinese-based APT which targeted governmental entities, hidden malware that was spotted behind legitimate-looking apps, a new version of Chinese espionage that was propagated through USB devices and malicious firmware implants discovered on internet routers. In addition, cybercriminals continue to leverage the latest AI revolution, by stretching the borders of generative AI chat platforms such as ChatGPT4.
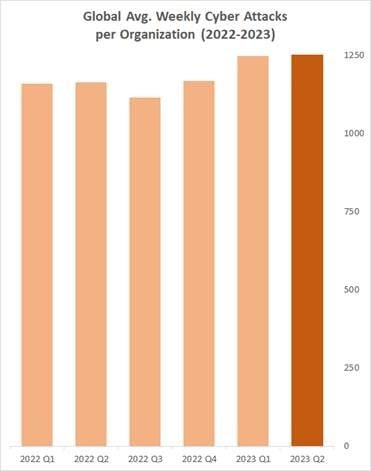
Overall Global Attacks – Highest number noted by Check Point Research in the past 2 years
In Q2 2023, there was an eight per cent increase in global average weekly attacks compared to the previous year. The average number of attacks per organisation per week reached 1,258 attacks – the highest number noted by Check Point Research in the past two years.
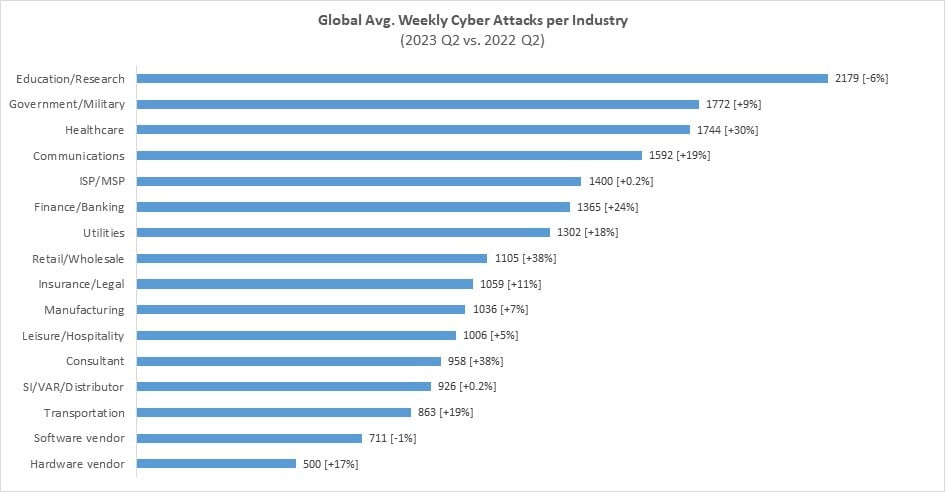
During Q2 2023, the Education/Research sector experienced the highest number of attacks, with an average of 2,179 attacks per organisation per week, marking a six per cent decrease compared to Q2 2022. The Government/Military sector was the second most attacked, with an average of 1,772 attacks per week, which represents a nine per cent increase from the parallel period last year. The Healthcare sector followed closely behind, with an average of 1,744 attacks per week, reflecting a significant YoY increase of 30 per cent.
During Q2 2023, Africa experienced the highest average number of weekly cyber-attacks per organisation, with an average of 2,164 attacks. This signifies a significant year-on-year increase of 23 per cent compared to the same period in 2022. The APAC region also witnessed a substantial 22 per cent YoY increase in the average number of weekly attacks per organisation, reaching an average of 2,046 attacks.
The different regions, their weekly average of attacks per organisation and YoY change (per cent) as shown:
- Africa: 2,164 (+23 per cent)
- APAC: 2,046 (+22 per cent)
- North America: 1,011 (+18 per cent)
- Latin Americas: 1,745 (+9 per cent)
- Europe: 1,013 (+5 per cent)
Ransomware Attacks per Region
In Q2 2023, one out of every 44 organisations worldwide experienced a ransomware attack, representing a decrease of nine per cent compared to Q2 2022, where one out of every 40 organisations suffered from such attacks. APAC and Europe sees significant Year Over Year increase in Ransomware attacks per organisation, with a 29 per cent and 21 per cent increase respectively. The North American region follows with a 15 per cent Year over year increase.
The different regions, organisation attacked ratio (1:X) and YoY change as shown:
- APAC: 1 out of 26 (+29 per cent)
- Europe: 1 out of 54 (+21 per cent)
- North America: 1 out of 94 (+15 per cent)
- Africa: 1 out of 30 (-30 per cent)
- Latin Americas: 1 out of 26 (-12 per cent)
Global ransomware attacks per industry: Cybercriminals are after government and military organisations
In Q2 2023, the Government/ Military sector experienced the highest number of ransomware attacks, with one out of every 25 organisations impacted, marking a slight four per cent decrease compared to the previous year. The Healthcare sector was the second most affected, with one out of every 27 organisations experiencing such attacks, representing an increase of 16 per cent YoY. The Education/ Research industry followed closely behind, with one out of every 31 organisations affected by ransomware, indicating a decrease of two per cent over the past year.
The different industries, organisation attacked ratio (1:X) and YoY change as shown:
- Consultant: 1 out of 38 (+128 per cent)
- Insurance/Legal: 1 out of 47 (+71 per cent)
- Utilities: 1 out of 37 (+60 per cent)
- Transportation: 1 out of 49 (+43 per cent)
- Leisure/Hospitality: 1 out of 55 (+41 per cent)
- Finance/Banking: 1 out of 31 (+33 per cent)
- Communications: 1 out of 37 (+24 per cent)
- Healthcare: 1 out of 27 (+16 per cent)
- SI/VAR/Distributor: 1 out of 41 (+15 per cent)
- Software vendor: 1 out of 65 (+13 per cent)
- Hardware vendor: 1 out of 73 (+7 per cent)
- ISP/MSP: 1 out of 36 (+2 per cent)
- Manufacturing: 1 out of 48 (+0.30 per cent)
- Education/Research: 1 out of 31 (-2 per cent)
- Government/Military: 1 out of 25 (-4 per cent)
- Retail/Wholesale: 1 out of 60 (-11 per cent)
Cyber Safety Tips
- Up-to-Date Patches: Keeping computers and servers up-to-date and applying security patches, especially those labelled as critical, can help to limit an organisation’s vulnerability to cyberattacks
- Cyber Awareness Training: Frequent cybersecurity awareness training is crucial to protecting the organisation against cyberattacks. This training should instruct employees to do the following:
- Do not click on malicious links
- Never open unexpected or untrusted attachments
- Avoid revealing personal or sensitive data to phishers
- Verify software legitimacy before downloading it
- Never plug an unknown USB into their computer
- Strengthening User Authentication: Cybercriminals commonly use the Remote Desktop Protocol (RDP) and similar tools to gain remote access to an organisation’s systems using guessed or stolen login credentials. Once inside, the attacker can drop ransomware on the machine and execute it, encrypting the files stored there. This potential attack vector can be closed through the use of strong user authentication. Enforcing a strong password policy, requiring the use of multi-factor authentication, and educating employees about phishing attacks designed to steal login credentials are all critical components of an organisation’s cybersecurity strategy.
- Keep your software updated. Attackers sometimes find an entry point within your apps and software, noting vulnerabilities and capitalising on them. Fortunately, some developers are actively searching for new vulnerabilities and patching them out. If you want to make use of these patches, you need to have a patch management strategy in place—and you need to make sure all your team members are constantly up to date with the latest versions.
- Choose Prevention over detection: Many claim that attacks will happen, and there is no way to avoid them, and therefore the only thing left to do is to invest in technologies that detect the attack once it has already breached the network and mitigate the damage as soon as possible. This is not true. Not only can attacks be blocked, but they can be prevented, including zero-day attacks and unknown malware. With the right technologies in place, most attacks, even the most advanced ones, can be prevented without disrupting the normal business flow.
- Anti-Ransomware Solutions: Some ransomware operators use well-researched and highly targeted spear phishing emails as their attack vector. These emails may trick even the most diligent employee, resulting in ransomware gaining access to an organisation’s internal systems. Protecting against this ransomware that “slips through the cracks” requires a specialised security solution. To achieve its objective, ransomware must perform certain anomalous actions, such as opening and encrypting large numbers of files. Anti-ransomware solutions monitor programmes running on a computer for suspicious behaviours commonly exhibited by ransomware, and if these behaviours are detected, the program can take action to stop encryption before further damage can be done.
Source: Check Point Research




